Staying on top of HIPAA (Health Insurance Portability and Accountability Act) is vital for any entity dealing with protected health data. This checklist provides a roadmap for healthcare providers, plans, and business partners to navigate these rules. Following these steps means securing patient info, boosting privacy and security, and avoiding hefty fines.
This checklist lays out how to see if HIPAA applies to your organization. It covers appointing the right roles, like a Privacy Officer. It tells you what audits to do and procedures to put in place. From breach notification protocols to implementing safeguards – this guide ensures full compliance coverage. By properly managing HIPAA duties, you maintain trust, protect your reputation, and are ready for regulatory scrutiny.
HIPAA Compliance for Organizations
First, determine if your operations are covered under HIPAA’s Administrative Simplification rules. The key is whether you electronically process health data for transactions where HIPAA standards apply.
Applicability of HIPAA
HIPAA or Health Insurance Portability and Accountability Act applies mainly to certain entities in healthcare. These are health plans, healthcare clearinghouses, and healthcare providers who transmit electronic health information. But this electronic transmission must relate to standard HIPAA transactions which define the act’s scope.
HIPAA-covered entities must follow its strict standards and protect patient information confidentiality. HIPAA provides a framework to secure patient data during electronic transactions and gives guidelines on how involved parties should handle healthcare information securely.
Covered Entities
HIPAA defines “Covered Entities” meeting certain criteria as obligated to comply with its privacy and security rules. However, some exceptions exist, such as health plans that provide only excluded benefits and are not covered entities. Also, campus health centers serving only students and non-electronic paper-to-paper fax transmissions are not considered electronic transmissions under HIPAA standards.
It’s crucial to grasp HIPAA’s reach. Though healthcare entities fall under its rules, not all are automatically Covered Entities. Knowing if an entity fits these definitions clarifies needed compliance safeguards for protecting sensitive health data effectively. This is key for maintaining patient data privacy and security per federal law.
Business Associates
HIPAA terms define business partners providing services to/for Covered Entities as Business Associates, bound by specific Administrative Simplification provisions. Usually, they must follow the Security Rule, Breach Notification requirements, and Privacy Rule sections outlined in Business Associate Agreements.
Not every business partner is a Business Associate; it applies if they create, get, keep, or send Protected Health Information (PHI) for HIPAA-regulated functions. Services without PHI handling are exempt from the Administrative Simplification provisions.
Exceptions for Workforce Members
Workforce linked to Covered Entities or Business Associates also have HIPAA exceptions. Paid staff or volunteers under these entities’ direct control aren’t Business Associates. Yet they must follow HIPAA rules for their organizational roles. The entities govern compliance via internal policies, ensuring all PHI handlers maintain HIPAA standards.
HIPAA rules show how the law handles different people in healthcare and related groups. It divides people into two groups: Business Associates and direct workers. This lets HIPAA have different rules for each group based on how much they work with patient health info. Direct workers may see more, so they have stricter rules. But Business Associates know what they must do, too. This makes sure everyone knows how to protect patient privacy no matter their role.
Special Circumstances for Non-Qualified Entities
Sometimes a health plan or provider is not a Covered Entity because of an exception. But if they work with a Covered Entity, they still have to follow some HIPAA rules. Like the Security Rule on keeping data safe, and rules for reporting breaches. Plus any Privacy Rule parts their Business Associate Agreement requires.
These HIPAA basics cover the key points. First, you need to know if your group is a Covered Entity or Business Associate. Then, you know what HIPAA rules apply based on that status.
HIPAA Privacy Rule Overview
The HIPAA Privacy Rule sets national standards protecting individuals’ medical records and other personal health info (PHI). It covers oral, written, or electronic PHI. Covered Entities must guard PHI rigorously, ensuring individuals’ privacy.
The rule requires safeguards preserving PHI privacy and limits use or disclosure without consent. Plus, it empowers individuals, giving control over their PHI – accessing, correcting, and transferring data between healthcare providers.
Importantly, individuals can get an accounting of disclosures – a detailed record of how their PHI was used or shared over six years (barring permitted disclosures).
Implementing the Privacy Rule
Though fewer organizations face the Privacy Rule versus the Security Rule, starting with HIPAA privacy checklists is wise. This privacy rights foundation is key for overall HIPAA compliance.
A thorough HIPAA Privacy Rule checklist should include the following:
- Appoint a HIPAA Privacy Officer to develop, implement, enforce HIPAA privacy policies.
- Grasp what PHI entails, when it can be shared under HIPAA rules, and when consent is mandatory.
- Pinpoint potential risks to PHI’s privacy and implement safeguards deemed reasonable and appropriate.
- Establish policies regulating PHI’s use and disclosure, adhering to HIPAA guidelines to prevent breaches.
- Set procedures for obtaining individual authorizations and allowing individuals to agree or object to specific uses of the PHI.
- Distribute a notice explaining how PHI is utilized and disclosed and outlining individuals’ rights over their information.
- Formulate policies for handling requests for PHI access, corrections, and transfers.
- Implement procedures for workforce members to report violations and for the organization to manage breach notifications.
- Educate the entire workforce on relevant policies and general compliance with HIPAA.
- Communicate consequences for not adhering to the organization’s HIPAA policies.
- Review and update Business Associate Agreements as needed.
- Document a contingency plan to address emergencies compromising systems or physical areas where PHI is stored.
Organizations should carefully follow these rules to fully obey the HIPAA Privacy Rule. Doing this protects patient information and upholds patient rights properly.
You might also like
business-intelligence
Making Supply Chain Resilience: AI Strategies
The COVID-19 pandemic changed global supply chains a lot. Company boards and CEOs now want supply chain leaders to reduce risks. They want supply chains to be ready for disruptions like this in the future. Our research at big companies like Walmart, Tyson Foods, Koch Industries, Maersk, Siemens, and Unilever shows how important advanced AI […]
Essentials of a HIPAA Risk Assessment Checklist
Before diving into different HIPAA compliance checklists, you need to know about a HIPAA risk assessment checklist. The size and skills of Covered Entities and Business Associates vary a lot. This means one risk analysis method won’t work for all. Even so, the Department of Health and Human Services (HHS) gives some goals for doing a HIPAA risk assessment.
Components of a HIPAA Risk Assessment:
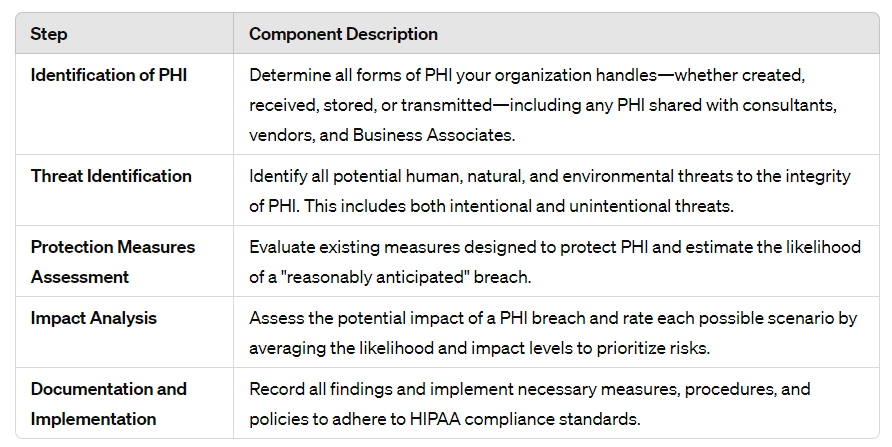
This guide breaks down HIPAA risk assessment into key steps. It shows you how to properly evaluate risks and implement needed safeguards.
Regular Compliance and Recordkeeping
HIPAA risk assessment isn’t a one-time event. It would help if you revisited it often to uphold HIPAA standards. Document the reasons behind your measures, procedures, and policies. Save all relevant policy documents for at least six years.
Flexible Approach and Tools
The HIPAA risk assessment process can differ greatly for each organization’s unique circumstances. Fortunately, online tools can assist in assembling this assessment. However, since HHS lacks a specific risk analysis method, these tools require tailoring to an organization’s needs.
Consistently reviewing and updating the HIPAA risk assessment is vital, especially when changes in workforce, practices, or tech could impact PHI security. This continuous assessment maintains HIPAA compliance across various areas.
HIPAA Security Rule Compliance Checklist
The HIPAA Security Rule safeguards electronically protected health information (ePHI). Divided into five key sections, it ensures confidentiality, integrity, and availability. Each section targets different ePHI security aspects. These tables outline the main requirements and guidelines for comprehensive compliance.
Understanding the Core Requirements: The General Rules
The General Rules section forms the Security Rule’s foundation. It focuses on overall obligations and frameworks for securing ePHI. This section emphasizes the need for Covered Entities and Business Associates to:
- Protect against reasonably anticipated threats or hazards to the security or integrity of ePHI.
- Guard against impermissible uses or disclosures not allowed under the Privacy Rule.
- Ensure that the workforce complies with the Security Rule.
Organizations must continuously assess potential threats and vulnerabilities. They must adjust security measures accordingly. This flexible approach allows organizations to tailor security practices based on size, capabilities, and the nature of handled ePHI.

Key Protocols: The Administrative Safeguards
The Administrative Safeguards are crucial in HIPAA’s Security Rule. They focus on managing the workforce’s actions and behavior. This relates to securing electronically protected health information (ePHI). One requirement is appointing a security official. This person oversees strategies protecting ePHI. They enforce policies and update them as needed. This is based on security landscape or organizational changes.
Conducting risk analyses regularly is very important. These analyses pinpoint potential vulnerabilities in ePHI protection. They help create strategies to mitigate risks. Employee training programs are equally key. These educate the workforce on their roles. They keep employees informed about security practices. Rules and requirements for compliance are also covered. Together, these safeguards maintain ePHI security rigorously. This upholds sensitive health information’s integrity and confidentiality.

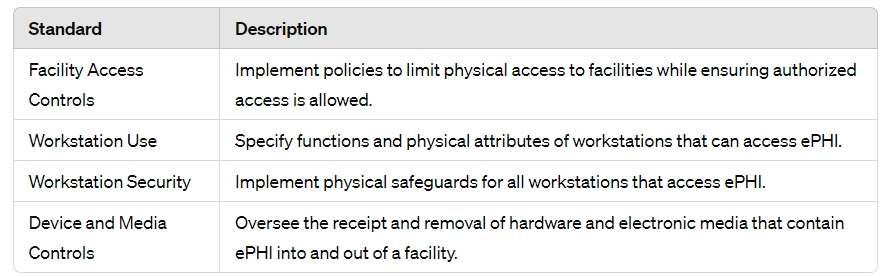
Essential Measures: The Physical Safeguards
The Physical Safeguards aim to control access to electronic Protected Health Information (ePHI). They restrict entry to areas and devices containing ePHI. These measures prevent unauthorized access, tampering, or theft. Access is limited to authorized personnel: Secure rooms, data centers, and policies govern device/media movement with ePHI. The Safeguards extend beyond access controls. Organizations monitor who enters ePHI facilities and how. Methods ensure physical protection, like visitor logs, security staff, and facilities resistant to unauthorized entry. Establishing robust oversight mitigates exposure risk and enhances ePHI handling security.
Furthermore, the Physical Safeguards extend beyond straightforward access controls. Moreover, organizations must validate who accesses ePHI locations, how access is granted, and processes for protecting information physically. In short, this includes visitor logs, deploying security workers, and sustaining resistant facilities restricting unauthorized entry. After all, implementing these sturdy physical blocks and oversight mechanisms considerably diminishes unauthorized disclosure risks, thereby enhancing overall ePHI handling security postures.
Critical Controls: The Technical Safeguards
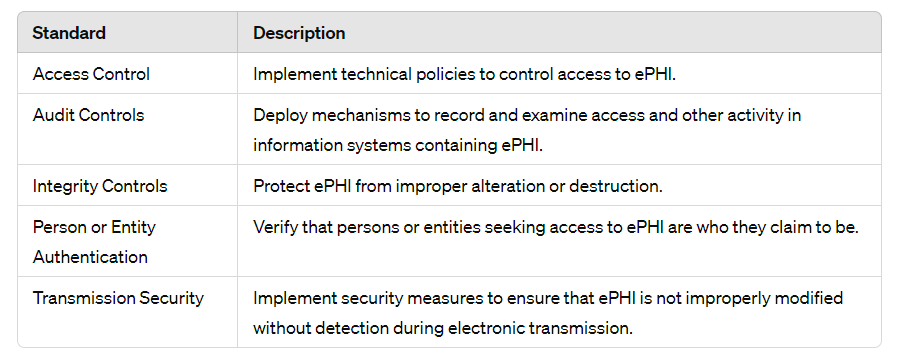
The Technical Safeguards form an integral HIPAA Security Rule component, securing ePHI from unauthorized individuals. Advanced technologies control and monitor ePHI electronic access pathways and transfers. For instance, encryption protocols, secure communication channels, and authentication verifying access authorization. In essence, the Safeguards leverage sophisticated methodologies to limit ePHI access solely to approved personnel.
The Technical Safeguards protect ePHI’s integrity when transmitted electronically. The integrity controls and transmission security prevent interception, alteration, or deletion. They ensure modifications or destruction are detected quickly, and data stays accurate. Keeping ePHI secure upholds HIPAA standards and builds trust between providers and patients.
Following these sections and specific standards helps organizations meet the HIPAA Security Rule’s comprehensive requirements. ePHI is effectively secured against threats and unauthorized access.
Organizational Requirements Under HIPAA
HIPAA’s Security Rule has key sections called Organizational Requirements. They give guidelines for administrative simplification. Unlike sections focusing on hybrid entities and health plans’ disclosures, Organizational Requirements broadly apply to most Covered Entities and Business Associates. They mainly concern Business Associate Agreements.
These Agreements ensure third parties handling ePHI comply with HIPAA’s Security Rule. They must require Business Associates to follow relevant Security Rule sections. If Business Associates subcontract, they need similar agreements with subcontractors, extending HIPAA compliance through ePHI’s custody chain. Business Associates must report security incidents, including unsecured ePHI data breaches, to Covered Entities.
Also, specific Organizational Requirements dictate protocols when health plans disclose ePHI to plan sponsors, similar to hybrid entity protocols. Here are typical elements these agreements cover:
- Ensuring all parties comply with safeguards protecting ePHI, following the Security Rule.
- HIPAA has rules about what subcontractors must do when handling health info. They must follow security laws too.
- If a subcontractor has a breach, they must tell the main company right away.
- Companies have to keep records for a certain time in case there’s an audit.
The rules say how long documents must be kept. This is important for audits, as explained in the HIPAA Audit Checklist. The rules make sure all groups handling health data have strong security. This protects patient info when different organizations work together.
What is HIPAA Compliance?
HIPAA compliance means following the laws and rules in HIPAA’s Administrative Simplification Regulations. This applies unless a state or federal law is stricter or gives people more privacy rights. Companies must prevent any misuse or unauthorized sharing of health info. They must also secure data from threats, per the Privacy and Security Rules. This duty exists even without a specific rule covering that situation.
So, HIPAA compliance may go beyond basic rules. Companies might need extra policies and safeguards based on what they do, how they operate, and special cases. The goal is protecting the data however necessary.
Applicability and Flexibility in HIPAA Compliance
HIPAA standards are quite complex, with different rules applying to different entities. Health plans, clearinghouses, providers, and Business Associates all face distinct compliance requirements based on their operations. One key factor is applicability – knowing which HIPAA standards you must follow.
Another crucial aspect is flexibility. HIPAA allows entities to tailor security measures using factors like organization size, staff capabilities, existing IT systems, cost concerns, and risk assessments. The goal is practical, effective compliance without waste or gaps. This flexibility demands careful implementation but is vital for robust, sustainable HIPAA compliance.
- An entity’s scale drives security approaches. Small firms react differently than large, complex ones.
- Available skills affect which control make sense. Leverage your team’s expertise.
- Legacy systems may lack advanced security features. Factor in technical limitations.
- Compliance budgets vary. Cost-effectiveness matters as much as stringent safeguards.
- Some risks warrant more rigorous protections than others. Prioritize based on threat likelihood and impact.
The flexible approach isn’t an excuse for noncompliance but a path to sensible implementation catered to each entity’s circumstances. Balancing this flexibility with HIPAA’s core privacy and security principles poses an ongoing challenge for entities of all types and sizes.
How to Achieve HIPAA Compliance
While a universal HIPAA checklist doesn’t exist, foundational principles guide compliance across Covered Entities, Business Associates, and Personal Health Record providers. The paramount goal – safeguarding individually identifiable health data – requires ensuring ePHI confidentiality, integrity, and availability through rigorous privacy and security controls tailored to each organization.
Organizations must adapt HIPAA compliance checklists to their operations. This article outlined key aspects of these checklists. But, if compliance measures seem insufficient, consult a professional HIPAA advisor. This ensures thorough efforts aligned with requirements, protecting patient information effectively.